Summary
This website contacted 7 IPs in 3 countries across 8 domains to perform 42 HTTP transactions. The main domain is login.microsoftonline.com and was registered NaN years ago.
Submitted URL: https://enterpriseenrollment.transpay.com
Effective URL: https://login.microsoftonline.com/organizations/oauth2/v2.0/authorize?client_id=c44b4083-3bb0-49c1-b47d-974e53cbdf3c&scope=https%3A%2F%2Fmanagement.core.windows.net%2F%2F.default%20openid%20profile%20offline_access&redirect_uri=https%3A%2F%2Fintune.microsoft.com%2Fauth%2Flogin%2F&client-request-id=019ba741-b852-7ece-a07f-0597e0eac5a4&response_mode=fragment&client_info=1&nonce=019ba741-b852-71b7-ab4c-ab91af5ee598&state=eyJpZCI6IjAxOWJhNzQxLWI4NTItN2QyNS1hZWVkLWIxODM0ODU0MzNkNyIsIm1ldGEiOnsiaW50ZXJhY3Rpb25UeXBlIjoicmVkaXJlY3QifX0%3D&x-client-SKU=msal.js.browser&x-client-VER=4.21.0&response_type=code&code_challenge=xB0GyfNLEDj7ndfWU3qJTxd43pHDI5FRwZcxoDtdEak&code_challenge_method=S256&site_id=501430&instance_aware=true&sso_reload=trueRedirected
AI Security Verdict
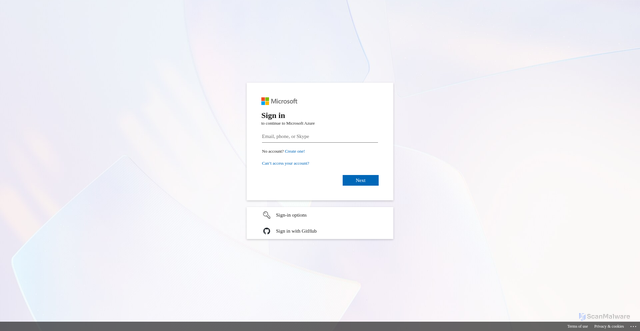
High Risk
Confidence: 82%
Suspicious login page impersonating Microsoft; likely phishing for credentials.
Risk Factors
Details
Page Title
Sign in to Microsoft Azure
Scan Type
public
Language
English
Category
technology software
(78%)Domain Information
Within the commercial generic top-level domain (.com), 'enterpriseenrollment.transpay.com' is registered with subdomain 'enterpriseenrollment'. The second-level label 'transpay' is 8 characters long with two vowels and 6 consonants. Segmentation suggests two words: trans, pay. The median word length lands at four characters. No strong language cues emerged from the frequency lists.
Screenshot
Page Load Overview
Language Analysis
Primary Language
Detection Details
Website Classification
Primary Category
All Detected Categories
Detected Features
Domain & IP Information
| Requests | IP Address | Location | AS Autonomous System |
|---|---|---|---|
| 1 | 150.171.84.26 | United States | AS8075MICROSOFT-CORP-MSN-AS-BLOCK |
| 1 | 20.91.147.72 | Sweden | AS8075MICROSOFT-CORP-MSN-AS-BLOCK |
| 1 | 13.107.246.44 | United States | AS8075MICROSOFT-CORP-MSN-AS-BLOCK |
| 1 | 40.126.31.1 | Sweden | |
| 1 | 2.21.239.142 | Unknown | |
| 1 | 40.126.32.133 | Amsterdam, North Holland, Netherlands | AS8075MICROSOFT-CORP-MSN-AS-BLOCK |
| 1 | 20.189.173.13 | Unknown | |
| 7 | 7 | - | - |
Detected Technologies5
Content Similarity HashesFor malware variant detection
TLSH (Trend Micro Locality Sensitive Hash)
Security-focusedSpecialized for malware detection and similarity analysis
ssdeep (Context Triggered Piecewise Hashing)
Context-awareDetects similar content even with modifications
sdhash (Similarity Digest Hashing)
High-precisionHigh-precision similarity detection for forensic analysis
These hashes enable detection of similar websites and malware variants by comparing content similarity even when exact matches aren't found.
Image Hashes
Perceptual Hashes
Other Hashes
Scan History
Scan history not available
Unable to load historical scan data