Summary
This website contacted 26 IPs in 2 countries across 7 domains to perform 11 HTTP transactions. The main domain is bafybeihqsfz4c5jqmr2jejdxob2xnmyxpxgz6akgz7s6dqp2fdlggjkzca.ipfs.dweb.link.
Submitted URL: https://bafybeihqsfz4c5jqmr2jejdxob2xnmyxpxgz6akgz7s6dqp2fdlggjkzca.ipfs.dweb.link/
The Cisco Umbrella rank of the primary domain is #174,969 of the top 1 million websites
AI Security Verdict
Confirmed Scam
Confidence: 95%
High‑risk phishing site harvesting credentials; report as scam.
Risk Factors
Details
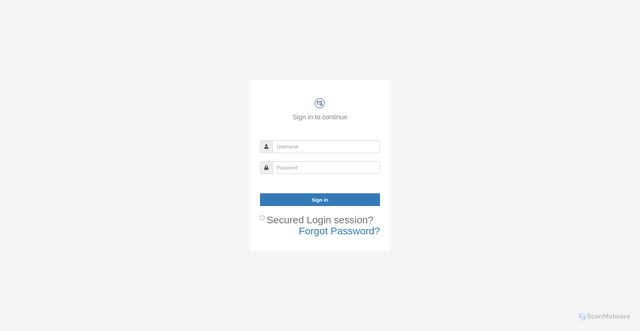
Page Title
Webmail Portal Access
Scan Type
public
Language
English
Category
phishing scam
(34%)Domain Information
Within the .link top-level domain, 'bafybeihqsfz4c5jqmr2jejdxob2xnmyxpxgz6akgz7s6dqp2fdlggjkzca.ipfs.dweb.link' is registered; it also runs on subdomain 'bafybeihqsfz4c5jqmr2jejdxob2xnmyxpxgz6akgz7s6dqp2fdlggjkzca.ipfs'. The registrable portion 'dweb' spans 4 characters containing 1 vowel alongside 3 consonants. It segments into two words: d, web. Median word length comes out to two characters. No strong language cues emerged from the frequency lists.
Screenshot
Page Load Overview
Language Analysis
Primary Language
Detection Details
Website Classification
Primary Category
All Detected Categories
Detected Features
Domain & IP Information
| Requests | IP Address | Location | AS Autonomous System |
|---|---|---|---|
| 3 | 209.94.90.3 | United States | AS40680PROTOCOL |
| 3 | 104.18.11.207 | United States | AS13335CLOUDFLARENET |
| 2 | 151.101.130.137 | San Francisco, California, United States | AS54113FASTLY |
| 1 | 142.250.185.138 | United States | AS15169GOOGLE |
| 1 | 104.17.25.14 | United States | AS13335CLOUDFLARENET |
| 1 | 172.67.139.119 | United States | AS13335CLOUDFLARENET |
| 0 | 151.101.194.137 | San Francisco, California, United States | AS54113FASTLY |
| 0 | 209.94.90.2 | United States | AS40680PROTOCOL |
| 0 | 104.18.10.207 | United States | AS13335CLOUDFLARENET |
| 0 | 151.101.66.137 | San Francisco, California, United States | AS54113FASTLY |
| 11 | 26 | - | - |
Detected Technologies4
Content Similarity HashesFor malware variant detection
Image Hashes
Perceptual Hashes
Other Hashes
Scan History
Scan history not available
Unable to load historical scan data