Summary
This website contacted 30 IPs in 4 countries across 10 domains to perform 16 HTTP transactions. The main domain is .
Submitted URL: https://t.co/SNX1qyz1E7
Effective URL: blob:https://platensefc.com/deceeb5f-cd10-4c0c-9da0-1461f35c141dRedirected
AI Security Verdict
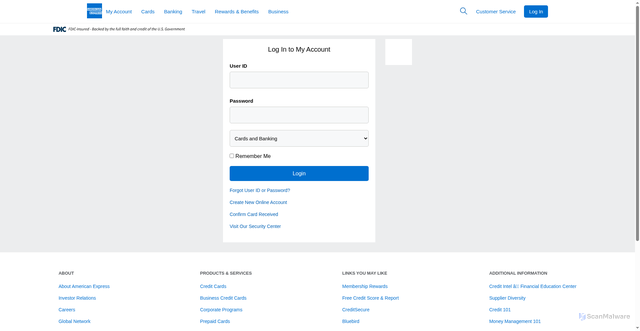
Confirmed Scam
Confidence: 95%
Phishing page impersonating American Express on an unranked, likely new domain – confirmed scam.
Risk Factors
Details
Page Title
Log in to My Account | American Express US
Scan Type
public
Language
English
Category
finance banking
(30%)Domain Information
Within the Colombian country-code top-level domain (.co), 't.co' is registered while skipping any subdomain. Its registrable label 't' stretches across 1 characters containing zero vowels alongside 1 consonant. Word splitting yields one word: t. Expect 1 character per word on average. Most frequently, 't' shows up in Chinese (Zhuyin). You may catch it in Catalan and Albanian as well. Taken together, it feels Chinese (Zhuyin) with single-word simplicity.
Screenshot
Page Load Overview
Language Analysis
Primary Language
Detection Details
Website Classification
Primary Category
All Detected Categories
Detected Features
Domain & IP Information
| Requests | IP Address | Location | AS Autonomous System |
|---|---|---|---|
| 16 | 23.201.242.36 | Frankfurt am Main, Hesse, Germany | AS16625AKAMAI-AS |
| 0 | 66.235.200.147 | United States | AS13335CLOUDFLARENET |
| 0 | 35.157.26.135 | Frankfurt am Main, Hesse, Germany | AS16509AMAZON-02 |
| 0 | 142.250.74.202 | United States | AS15169GOOGLE |
| 0 | 172.66.0.227 | United States | AS13335CLOUDFLARENET |
| 0 | 23.227.39.200 | Ottawa, Ontario, Canada | AS13335CLOUDFLARENET |
| 0 | 151.101.130.137 | San Francisco, California, United States | AS54113FASTLY |
| 0 | 188.114.96.3 | United States | AS13335CLOUDFLARENET |
| 0 | 104.17.25.14 | United States | AS13335CLOUDFLARENET |
| 0 | 2606:4700::6811:180e | United States | AS13335CLOUDFLARENET |
| 16 | 30 | - | - |
Detected Technologies7
Content Similarity HashesFor malware variant detection
TLSH (Trend Micro Locality Sensitive Hash)
Security-focusedSpecialized for malware detection and similarity analysis
ssdeep (Context Triggered Piecewise Hashing)
Context-awareDetects similar content even with modifications
sdhash (Similarity Digest Hashing)
High-precisionHigh-precision similarity detection for forensic analysis
These hashes enable detection of similar websites and malware variants by comparing content similarity even when exact matches aren't found.
Image Hashes
Perceptual Hashes
Other Hashes
Scan History
Scan history not available
Unable to load historical scan data